OpenSSH 8.6 is now available. The 'ssh-rsa' signature scheme, which usesthe SHA-1 hash algorithm, will be disabled by default in the nearfuture. 'Note that the deactivation of 'ssh-rsa' signatures does notnecessarily require cessation of use for RSA keys. In the SSH protocol,keys may be capable of signing using multiple algorithms. In particular,'ssh-rsa' keys are capable of signing using 'rsa-sha2-256' (RSA/SHA256),'rsa-sha2-512' (RSA/SHA512) and 'ssh-rsa' (RSA/SHA1). Only the last ofthese is being turned off by default.
The System Administrator's Guide documents relevant information regarding the deployment, configuration, and administration of Red Hat Enterprise Linux 7. It is oriented towards system administrators with a basic understanding of the system. To expand your expertise, you might also be interested in the Red Hat System Administration I (RH124), Red Hat System Administration II (RH134), Red Hat. OpenSSH is the premier connectivity tool for remote login with the SSH protocol. It encrypts all traffic to eliminate eavesdropping, connection hijacking, and other attacks. In addition, OpenSSH provides a large suite of secure tunneling capabilities, several authentication methods, and sophisticated configuration options. Cd /etc/ssh/ chmod 400 sshhostecdsakey sshhosted25519key sshhostrsakey echo 'PermitRootLogin yes' /etc/ssh/sshdconfig echo 'PasswordAuthentication yes' /etc/ssh/sshdconfig systemctl restart sshd. 注意:升级后重启SSH可能出现以下错误: It is required that your private key files are NOT accessible by others. OpenSSH Configuration Files. OpenSSH has two different sets of configuration files: one for client programs (ssh, scp, and sftp) and one for the server daemon (sshd). System-wide SSH configuration information is stored in the /etc/ssh/ directory. OpenSSH is a BSD/Linux implementation of SSH1 and SSH2 for encrypted terminal connections, tunneling and file transfers. It includes the sshd server, scp and sftp, and various utility tools such as ssh-add, ssh-agent, ssh-keysign, ssh-keyscan, ssh-keygen, and the sftp-server.
'| From: | Damien Miller |
| To: | lwn-AT-lwn.net |
| Subject: | Announce: OpenSSH 8.6 released |
| Date: | Sun, 18 Apr 2021 18:53:14 -0600 |
| Message-ID: | <94b0350a0f8a1fac@cvs.openbsd.org> |
OpenSSH 8.6 released
Posted Apr 20, 2021 7:14 UTC (Tue) by wtarreau (subscriber, #51152) [Link]
The incessant switch between algorithms is a real pain. Initially we were all using RSA. Then we were told RSA was bad and that DSA had to be used instead. We all switched to DSA. Then DSA was deamed bad forcing many of us to turn back to RSA after facing connection issues on their machines, but with larger keys this time. Then ED25519 started to appear but is still not enabled on a wide number of already installed machines (typically the machines we have in our respective basements). Now RSA's dead again..SSH is widely used to connect, but not only where extreme security is required, simply where you need to connect (i.e. the old server on your local network, where it replaced telnet+ftp). In such situations removing support for algorithms breaks the connectivity, makes backups fail, and causes lots of grief. I think that clients should not completely remove support for no-so-old algorithm but instead require an extra option like '--insecure' or something like this. Because clearly if I can't connect anymore to some of my old machines, I'll go back to telnet, which never broke accessibility in 40 years. And I do think that SSH is better than telnet, even with older keys that a neighbor could fake for $50k to intercept my connection on my local network just to send me a 'you're pwned' banner when I connect..
OpenSSH 8.6 released
Posted Apr 20, 2021 7:39 UTC (Tue) by cjwatson (subscriber, #7322) [Link]
OpenSSH 8.6 released
Winamp encoder software. Posted Apr 20, 2021 8:21 UTC (Tue) by Sesse (subscriber, #53779) [Link]
RSA keys yes, but that isn't the problem: SSHing to your switch, where you cannot change the sshd implementation, is. (Keys can, after all, be replaced pretty easily!) This is a huge pain, and has only been accelerating in the last decade.Unable to negotiate with port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
I sometimes keep a machine on oldstable or oldoldstable around, so that I can have an older ssh(1) binary to SSH to stuff with…
OpenSSH 8.6 released
Posted Apr 20, 2021 9:20 UTC (Tue) by dottedmag (subscriber, #18590) [Link]

OpenSSH 8.6 released
Posted Apr 20, 2021 9:32 UTC (Tue) by Sesse (subscriber, #53779) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 10:38 UTC (Tue) by Cyberax (✭ supporter ✭, #52523) [Link]
Openssh 8.5 Download
OpenSSH 8.6 released
Posted Apr 20, 2021 8:41 UTC (Tue) by Vipketsh (guest, #134480) [Link]
A better example is some old(er) networking equipment, like a managed switch. These things are often disowned by their manufacturers so no hope to getting any update with more recent authentication schemes but the equipment works perfectly well for its intended function. I would be happy if they disabled rsa-ssh on the server and put it into some last-resort-fallback list on the client when negotiating the scheme.It would be great if security people today would understand that security is a function of *three* things: Confidentiality, Integrity and *Availability*. Clearly availability is being reduced here for no gain in Integrity.
OpenSSH 8.6 released
Posted Apr 20, 2021 10:14 UTC (Tue) by hkario (subscriber, #94864) [Link]
> Clearly availability is being reduced here for no gain in Integrity.That's your opinion, not shared by wider security community.
Look for SSH Downgrade Attacks to learn why.
OpenSSH 8.6 released
Posted Apr 20, 2021 10:43 UTC (Tue) by pizza (subscriber, #46) [Link]
> That's your opinion, not shared by wider security community.> Look for SSH Downgrade Attacks to learn why.
Sure, and the net result of this 'improved security' is 'SSH downgrade to telnet'
Mission accomplished, I guess.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:04 UTC (Tue) by hkario (subscriber, #94864) [Link]
First, count number of people that use SSH daily with modern ciphers and count how many people need to use long insecure protocols like SSHv1.Second, you aren't secure with SSHv1, at least with telnet you're not lying to yourself that you are. So there's a chance that you'll do something about it. That is improved security: real, not apparent.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:32 UTC (Tue) by pizza (subscriber, #46) [Link]
> That is improved security: real, not apparent.What is 'real, improved' over dropping the barrier of attack from $50K to $0?
Openssh 8.5
At $50K, you're only going to be vulnerable to larger criminal enterprises and nation-states that are specifically going after _you_. But at $0 you're open to every script kiddie on the internet with a copy of nmap.
Your argument is equivalent to getting rid of the front doors on houses because they're easy to open.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:40 UTC (Tue) by hkario (subscriber, #94864) [Link] R cheat sheet tidyverse.
OpenSSH 8.6 released
Posted Apr 22, 2021 17:39 UTC (Thu) by jschrod (subscriber, #1646) [Link]
No, you don't understand him.It seems that there are a lot of ssh use cases that you haven't experienced yet, especially in the network devices realm.
OpenSSH 8.6 released
Posted Apr 20, 2021 15:03 UTC (Tue) by foom (subscriber, #14868) [Link]
It's there any chance it isn't exploitable via some well known security vulnerabilities? Quite possibly even ones which have been nicely packaged into a one-click exploit toolkit, and a may be just as easy to 'login' with as an ssh client..
OpenSSH 8.6 released
Posted Apr 20, 2021 14:03 UTC (Tue) by epa (subscriber, #39769) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 16:53 UTC (Tue) by Vipketsh (guest, #134480) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 12:21 UTC (Tue) by pabs (subscriber, #43278) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 16:55 UTC (Tue) by floppus (subscriber, #137245) [Link] How much does capture one cost.
For $WORK we needed an inexpensive router with high IPSec throughput, and the option we settled on was a Mikrotik box, which runs some form of Linux but the crypto offload hardware is proprietary.Even when it comes to standard distros, though, dropbear added support for Ed25519 and RSA+SHA-2 only very recently, so those aren't yet supported in stable OpenWRT.
OpenSSH 8.6 released
Posted Apr 22, 2021 20:30 UTC (Thu) by Sesse (subscriber, #53779) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 20:32 UTC (Thu) by pabs (subscriber, #43278) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 20:36 UTC (Thu) by Sesse (subscriber, #53779) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 21:00 UTC (Thu) by pabs (subscriber, #43278) [Link]
There are folks trying to change this, here are a few of the Debian derivatives I know about, I think they mostly do enterprise stuff though:https://wiki.debian.org/Derivatives/Census/VyOS
https://wiki.debian.org/Derivatives/Census/DANOS
https://wiki.debian.org/Derivatives/Census/CumulusLinux
https://wiki.debian.org/Derivatives/Census/OpenNetworkLinux
OpenSSH 8.6 released
Posted Apr 20, 2021 13:32 UTC (Tue) by itvirta (guest, #49997) [Link]
Removing things from the enabled-by-default list doesn't prevent enabling them when needing to talk to ancientOpenssh 8.5 Crack
equipment. It wasn't too long ago I used something like 'ssh -c3des' (or even 'ssh -1') to connect to some such
relic. Per-host settings for Ciphers, Protocol, KexAlgorithms and such in '.ssh/config' also help if you need to do
that often.
The problem is downgrades that can happen automatically, within the the default-enabled settings.
(And downgrading to telnet probably doesn't fit there.)
OpenSSH 8.6 released
Posted Apr 20, 2021 18:54 UTC (Tue) by lamikr (subscriber, #2289) [Link]
If I create the ca.key and pem file with OpenSSL 1.1.1k which I believe is the latest release by using typical command shown in many examples: openssl req -new -x509 -keyout ca.key -out ca.pem -days 45 -config ./ca.cnf
and then check the cipher used with command:
openssl asn1parse -in ca.key
From the output I can see that the des is still used as a cipher:
64:d=4 hl=2 l= 8 prim: OBJECT :des-ede3-cbc
Shouldn't openssl use something more secure by default?
OpenSSH 8.6 released
Posted Apr 20, 2021 19:41 UTC (Tue) by tamiko (subscriber, #115350) [Link]
> Shouldn't openssl use something more secure by default?It should. But this is entirely orthogonal to openssh changing it's default-enabled cipher set.
OpenSSH 8.6 released
Posted Apr 22, 2021 17:42 UTC (Thu) by jschrod (subscriber, #1646) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 10:30 UTC (Thu) by jezuch (subscriber, #52988) [Link]
Doing something once every couple of years does not strike me as 'incessant', and moaning about this particular one strikes me as denying reality. The reality of security is that the attacks only get better and time is *not* your friend. Thus key rotation should be routine, not an inconvenient thing you're forced to by external events.What is sad is that the designers of the SSH protocol were also denying this reality. Support for *automatic* key rotation and upgrade should have been designed into the protocol from the start. It is not, so everyone has to do it manually (or automating it themselves) and everyone suffers and security suffers even more. So, in the end, I don't really blame you for moaning.
Obviously I have a couple of decades of hindsight to benefit from so I guess it turns me into a smart-ass at this point :)
OpenSSH 8.6 released
Posted Apr 22, 2021 11:42 UTC (Thu) by pizza (subscriber, #46) [Link]
> Support for *automatic* key rotation and upgrade should have been designed into the protocol from the start.Absolutely!
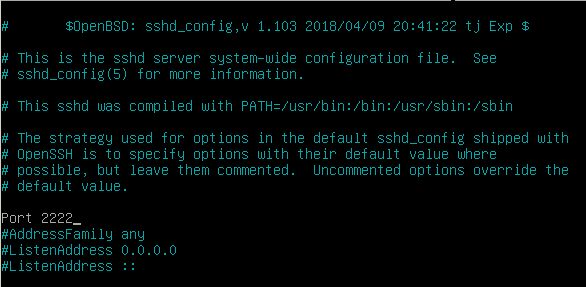
I'm in a situation where I have a gerrit instance using one of these these problematic host keys (generated back in 2011), mostly hit by tools (ie git) on systems I don't control. I can't replace that problematic key with a stronger one without requiring manual intervention on every single client that hits this thing. Bleh.
OpenSSH 8.6 released
Posted Apr 22, 2021 13:59 UTC (Thu) by grawity (subscriber, #80596) [Link]

I think that clients should not completely remove support for no-so-old algorithm but instead require an extra option like '--insecure' or something like this.
I somewhat agree with this, but, fortunately, OpenSSH isn't the only SSH client for Linux. PuTTY (specifically the 'plink' command) is actively maintained and has support for everything under the sun, from Ed448 to SUPDUP.
Current Description

OpenSSH 8.6 released
Posted Apr 20, 2021 9:32 UTC (Tue) by Sesse (subscriber, #53779) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 10:38 UTC (Tue) by Cyberax (✭ supporter ✭, #52523) [Link]
Openssh 8.5 Download
OpenSSH 8.6 released
Posted Apr 20, 2021 8:41 UTC (Tue) by Vipketsh (guest, #134480) [Link]
A better example is some old(er) networking equipment, like a managed switch. These things are often disowned by their manufacturers so no hope to getting any update with more recent authentication schemes but the equipment works perfectly well for its intended function. I would be happy if they disabled rsa-ssh on the server and put it into some last-resort-fallback list on the client when negotiating the scheme.It would be great if security people today would understand that security is a function of *three* things: Confidentiality, Integrity and *Availability*. Clearly availability is being reduced here for no gain in Integrity.
OpenSSH 8.6 released
Posted Apr 20, 2021 10:14 UTC (Tue) by hkario (subscriber, #94864) [Link]
> Clearly availability is being reduced here for no gain in Integrity.That's your opinion, not shared by wider security community.
Look for SSH Downgrade Attacks to learn why.
OpenSSH 8.6 released
Posted Apr 20, 2021 10:43 UTC (Tue) by pizza (subscriber, #46) [Link]
> That's your opinion, not shared by wider security community.> Look for SSH Downgrade Attacks to learn why.
Sure, and the net result of this 'improved security' is 'SSH downgrade to telnet'
Mission accomplished, I guess.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:04 UTC (Tue) by hkario (subscriber, #94864) [Link]
First, count number of people that use SSH daily with modern ciphers and count how many people need to use long insecure protocols like SSHv1.Second, you aren't secure with SSHv1, at least with telnet you're not lying to yourself that you are. So there's a chance that you'll do something about it. That is improved security: real, not apparent.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:32 UTC (Tue) by pizza (subscriber, #46) [Link]
> That is improved security: real, not apparent.What is 'real, improved' over dropping the barrier of attack from $50K to $0?
Openssh 8.5
At $50K, you're only going to be vulnerable to larger criminal enterprises and nation-states that are specifically going after _you_. But at $0 you're open to every script kiddie on the internet with a copy of nmap.
Your argument is equivalent to getting rid of the front doors on houses because they're easy to open.
OpenSSH 8.6 released
Posted Apr 20, 2021 11:40 UTC (Tue) by hkario (subscriber, #94864) [Link] R cheat sheet tidyverse.
OpenSSH 8.6 released
Posted Apr 22, 2021 17:39 UTC (Thu) by jschrod (subscriber, #1646) [Link]
No, you don't understand him.It seems that there are a lot of ssh use cases that you haven't experienced yet, especially in the network devices realm.
OpenSSH 8.6 released
Posted Apr 20, 2021 15:03 UTC (Tue) by foom (subscriber, #14868) [Link]
If you have a device that's so old it only runs sshv1 -- which presumably means it hasn't been updated in 20 years -- does it really matter what protocol you use to connect to it?It's there any chance it isn't exploitable via some well known security vulnerabilities? Quite possibly even ones which have been nicely packaged into a one-click exploit toolkit, and a may be just as easy to 'login' with as an ssh client..
OpenSSH 8.6 released
Posted Apr 20, 2021 14:03 UTC (Tue) by epa (subscriber, #39769) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 16:53 UTC (Tue) by Vipketsh (guest, #134480) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 12:21 UTC (Tue) by pabs (subscriber, #43278) [Link]
OpenSSH 8.6 released
Posted Apr 20, 2021 16:55 UTC (Tue) by floppus (subscriber, #137245) [Link] How much does capture one cost.
For $WORK we needed an inexpensive router with high IPSec throughput, and the option we settled on was a Mikrotik box, which runs some form of Linux but the crypto offload hardware is proprietary.Even when it comes to standard distros, though, dropbear added support for Ed25519 and RSA+SHA-2 only very recently, so those aren't yet supported in stable OpenWRT.
OpenSSH 8.6 released
Posted Apr 22, 2021 20:30 UTC (Thu) by Sesse (subscriber, #53779) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 20:32 UTC (Thu) by pabs (subscriber, #43278) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 20:36 UTC (Thu) by Sesse (subscriber, #53779) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 21:00 UTC (Thu) by pabs (subscriber, #43278) [Link]
There are folks trying to change this, here are a few of the Debian derivatives I know about, I think they mostly do enterprise stuff though:https://wiki.debian.org/Derivatives/Census/VyOS
https://wiki.debian.org/Derivatives/Census/DANOS
https://wiki.debian.org/Derivatives/Census/CumulusLinux
https://wiki.debian.org/Derivatives/Census/OpenNetworkLinux
OpenSSH 8.6 released
Posted Apr 20, 2021 13:32 UTC (Tue) by itvirta (guest, #49997) [Link]
Removing things from the enabled-by-default list doesn't prevent enabling them when needing to talk to ancientOpenssh 8.5 Crack
equipment. It wasn't too long ago I used something like 'ssh -c3des' (or even 'ssh -1') to connect to some such
relic. Per-host settings for Ciphers, Protocol, KexAlgorithms and such in '.ssh/config' also help if you need to do
that often.
The problem is downgrades that can happen automatically, within the the default-enabled settings.
(And downgrading to telnet probably doesn't fit there.)
OpenSSH 8.6 released
Posted Apr 20, 2021 18:54 UTC (Tue) by lamikr (subscriber, #2289) [Link]
If I create the ca.key and pem file with OpenSSL 1.1.1k which I believe is the latest release by using typical command shown in many examples: openssl req -new -x509 -keyout ca.key -out ca.pem -days 45 -config ./ca.cnf
and then check the cipher used with command:
openssl asn1parse -in ca.key
From the output I can see that the des is still used as a cipher:
64:d=4 hl=2 l= 8 prim: OBJECT :des-ede3-cbc
Shouldn't openssl use something more secure by default?
OpenSSH 8.6 released
Posted Apr 20, 2021 19:41 UTC (Tue) by tamiko (subscriber, #115350) [Link]
> Shouldn't openssl use something more secure by default?It should. But this is entirely orthogonal to openssh changing it's default-enabled cipher set.
OpenSSH 8.6 released
Posted Apr 22, 2021 17:42 UTC (Thu) by jschrod (subscriber, #1646) [Link]
OpenSSH 8.6 released
Posted Apr 22, 2021 10:30 UTC (Thu) by jezuch (subscriber, #52988) [Link]
Doing something once every couple of years does not strike me as 'incessant', and moaning about this particular one strikes me as denying reality. The reality of security is that the attacks only get better and time is *not* your friend. Thus key rotation should be routine, not an inconvenient thing you're forced to by external events.What is sad is that the designers of the SSH protocol were also denying this reality. Support for *automatic* key rotation and upgrade should have been designed into the protocol from the start. It is not, so everyone has to do it manually (or automating it themselves) and everyone suffers and security suffers even more. So, in the end, I don't really blame you for moaning.
Obviously I have a couple of decades of hindsight to benefit from so I guess it turns me into a smart-ass at this point :)
OpenSSH 8.6 released
Posted Apr 22, 2021 11:42 UTC (Thu) by pizza (subscriber, #46) [Link]
> Support for *automatic* key rotation and upgrade should have been designed into the protocol from the start.Absolutely!
I'm in a situation where I have a gerrit instance using one of these these problematic host keys (generated back in 2011), mostly hit by tools (ie git) on systems I don't control. I can't replace that problematic key with a stronger one without requiring manual intervention on every single client that hits this thing. Bleh.
OpenSSH 8.6 released
Posted Apr 22, 2021 13:59 UTC (Thu) by grawity (subscriber, #80596) [Link]
I think that clients should not completely remove support for no-so-old algorithm but instead require an extra option like '--insecure' or something like this.
I somewhat agree with this, but, fortunately, OpenSSH isn't the only SSH client for Linux. PuTTY (specifically the 'plink' command) is actively maintained and has support for everything under the sun, from Ed448 to SUPDUP.
Current Description
Openssh 8.5 Rpm
ssh-agent in OpenSSH before 8.5 has a double free that may be relevant in a few less-common scenarios, such as unconstrained agent-socket access on a legacy operating system, or the forwarding of an agent to an attacker-controlled host.
Analysis Description
ssh-agent in OpenSSH before 8.5 has a double free that may be relevant in a few less-common scenarios, such as unconstrained agent-socket access on a legacy operating system, or the forwarding of an agent to an attacker-controlled host.
Severity
CVSS 3.x Severity and Metrics:Weakness Enumeration
| CWE-ID | CWE Name | Source |
|---|---|---|
| CWE-415 | Double Free | NIST |
Known Affected Software Configurations Switch to CPE 2.2
Denotes Vulnerable Software
Are we missing a CPE here? Please let us know.

